It has been a tough week for all those companies that have been attacked by Wanna Decrytor, also known as Ransomware. Many unknowns in the head, such as; What is? What are you doing? Why is it on everyone’s lips?
This malware; Answering the first question that we asked ourselves, it has had many mentions in the media, social networks, important blogs… Since large companies such as Telephone have been infected. Many will say or think because large companies like Telefónica have succumbed to this attack, they are supposed to be prepared…
How Ransomware Works
Over the years, data and information have become the great source of wealth for companies; what Wanna Decrytor does is simply hijack all this data.
The Ransomware is installed silently on mobile devices and computers of all kinds, and once it is put into action, it encrypts or encrypts all the data to block access to it without the password that allows it to be decrypted. In the new version, it takes advantage of a vulnerability in Windows, for which Microsoft published a patch in March, to spread throughout the network and infect all those computers that are connected to it.
The problem lies in the “Windows Server Message Block” (SMB) service that Windows computers use to share files and printers on a local network. Microsoft fixed the vulnerability with bulletin MS17-010..
The means that cybercriminals often use to spread this malware is through Social Engineering. It consists of deceiving the victim, a clear example would be spam emails: false receipts or invoices, job offers, security warnings or undeliverable email notices, etc…
If the victim opens the ZIP file that is usually attached to such emails, a malicious script is activated which causes the malware to be installed.
How to recover the data
As mentioned, Ransomware encrypts files with a password and for us to be able to obtain said password, cyber attackers ask for a ransom that is almost always cheap. As can be seen in the image, what the affected users see is usually an information screen in which an amount of money is requested that must be paid within a set period, or else that data will be blocked.
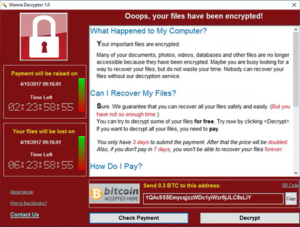
La única forma de recuperar los datos es pagando. A veces, incluso pagando, no es posible volver a acceder a la información encriptada.
Consejos de seguridad
El mejor consejo es realizar copia de seguridad periódicamente y que esta copia no este alojada en el mismo equipo si no en un disco duro externo, nube… Entre otras opciones.
Aquí les dejamos una serie de recomendaciones para evitar este y futuros problemas:
- NUNCA abra un correo electrónico de una fuente desconocida
- NUNCA abra un adjunto o enlace a web en un correo electrónico, si no estás 100% convencido.
- Use contraseñas seguras. Mayúsculas, minúsculas, números y signos. Renuévala frecuentemente y no la apunten en ningún sitio.
- Mantenga su equipo al día activando las actualizaciones automáticas.
- Disponer de sistemas de copias de seguridad tanto en local como en la nube.
Estas recomendaciones son básicas para tener un nivel alto de protección frente a estos ataques.





